Cloud SIEM and IDS
Cost-effective compliance solutions for insider threat management.
Overview
Our Cloud SIEM (Security Incident and Event Management) and IDS solution enables your organization to efficiently collect and analyze logs, system, and network metrics gathered from all your digital assets in one place. This capability allows you to recreate past incidents or analyze new ones to investigate suspicious activity and implement more effective security processes.
Built on a combination of open-source tools and proprietary scripts and processes, we’ve developed an efficient and cost-effective SIEM and IDS solution. Our service can replace your existing commercial point solutions with a single platform that works out-of-the-box and can be further customized to meet your organization’s requirements.
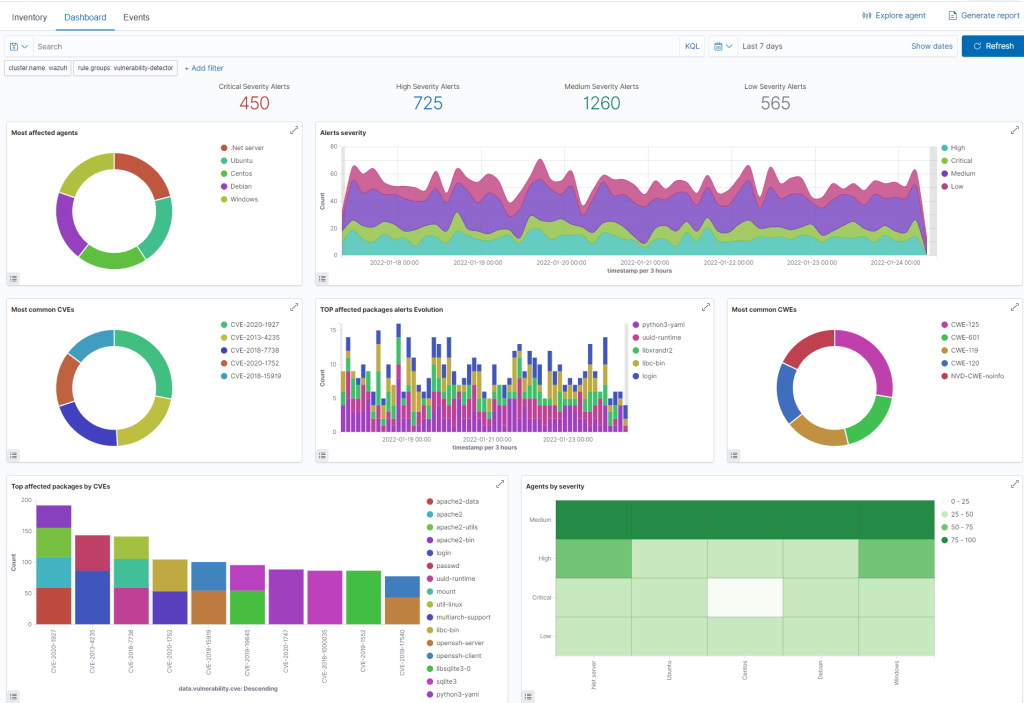
Cloud SIEM aggregates system, network, and audit logs from various sources, including firewalls, routers, network devices, NIDS, Windows, Linux/Unix, MacOS, databases, VMware ESX, mail servers, web servers, and more.
Cloud SIEM allows you to quickly review critical asset information required for compliance, increasing awareness of potential security risks, vulnerabilities, and threats within your organization.
Our SIEM service delivers essential security controls to achieve compliance with popular security frameworks such as ISO 27001, PCI DSS, SOC 2, NIST, HIPAA, GDPR, and more. Critical security information is visualized, with security incidents and threats made visible in high-level reports and dashboards for real-time reviews. Our reporting and dashboards include information from file integrity monitoring checks, collection of account management activities, and audit logs.
Continuous security monitoring swiftly detects policy violations, malicious activities targeting sensitive assets, and changes in critical files. Various report templates ensure that users can easily generate and distribute relevant reports in different formats (PDF, email, etc.) for regulatory compliance.
What are SIEM and IDS?
A SIEM (Security Incident and Event Management) system helps organizations detect potential security threats and vulnerabilities before they can disrupt business operations. By surfacing user behaviors and automating many manual processes associated with threat detection and incident response, SIEM has become an integral part of modern-day Security Operation Centers (SOCs) for compliance management and security management.
An Intrusion Detection System (IDS) is a system that monitors network traffic and devices for suspicious activity, issuing alerts when such activity is discovered. It is a software application that checks a network or system for harmful activity or policy violations. Malicious activities or violations are typically reported to administrators or collected centrally using a SIEM system. A SIEM system integrates outputs from multiple sources and uses alarm filtering techniques to differentiate malicious activity from false alarms.
Main Features
Here is a brief sample list of our solution’s detection and alerting capabilities:
- Threat intelligence feeds and detection of malicious actors (APTs)
- File Integrity Monitoring
- Brute Force Attack Detection
- Monitoring Cloud Security Posture: AWS, GCP, Azure
- Unauthorized Access Detection
- 3rd party Network IDS integrations
- SQL Injection Detection
- Detection of malware and suspicious binaries
- Support for YARA and SIGMA (Socprime) rules
- Detection and malware removal using VirusTotal
- Vulnerability Detection
- Detection of hidden and malicious process execution
- Security posture monitoring for GitHub, O365, Google Workspace
- Creation of custom rules and decoders
Ensure Compliance and Fulfill Contractual Obligations
Implementing an IDS for your corporate devices (workstations, laptops, etc.) and cloud workloads is a mandatory requirement across all security and auditing frameworks and standards.
ISO 27001 compliance requires the aggregation of event data from multiple systems and the security management of sensitive assets within an organization (SIEM). Our Cloud SIEM solution provides comprehensive event classification and detailed reporting mapped directly to the following compliance frameworks: SOC 2, ISO 27001, PCI DSS, NIST, HIPAA, GDPR.
While not all other security standards and frameworks explicitly specify the need for SIEM, most frameworks, including SOC, PCI, and NIST, include requirements for monitoring, logging, and security events management. These requirements are best met when an actual SIEM is implemented versus individual point solutions. In addition, most auditing teams prefer to see a SIEM deployed in your organization, which makes their job easier and reduces the friction between your organization and the auditing team. Having a SIEM is a must for medium and large enterprises and is often required by their risk assessment teams or outlined as a requirement in their legal agreements.
Implementing a SIEM and IDS for your cloud and corporate devices is nowadays required by most insurance companies in order for them to provide your organization with ransomware coverage and lower premiums.
Pricing
We offer flexible pricing with monthly and yearly tier commitments. The price depends on the number of assets monitored, your daily log ingestion, and preferred log retention rates.
Contact us today for a free trial and to receive a quote tailored to your needs.

Sign up for our newsletter
Get monthly news and new post alerts!
